WhyFind - Hack The Box

Scenario
We have been hot on the trail for a political dissident. They jump from café to café using the Wi-Fi making it hard to nab them. During one of their trips, they unknowingly sat next to one of our agents and we captured them with their laptop on. We need to know where they have been and what they have been doing. Analyze the KAPE output and see if you can get us some answers.
Documents Provided
- KAPEOUT.zip
Q1: What is the Computer name of the machine?
First I opened Autopsy to analyze this KAPE output, it will provide us a easy way to look at this KAPE output. So we create a new case and select the C/ folder inside the extraction provided.
Then Autopsy will identify some Data Artifacts one of these is Operating System Information:
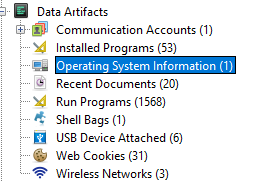
This will give us the information we need to answer the question.
Click to reveal the answer
Q2: What is the first Wi-Fi SSID(Decoded) they connected to on May 30th 2025?
Now we have to go to another artifact, in this case Wireless Networks:
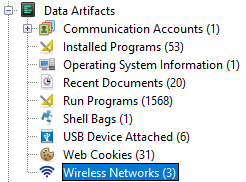
We will find 3 networks, it asks for the first one but checking the time all 3 have the same timestamp, so I just picked up the first one.
Click to reveal the answer
Q3: When did the system obtain a lease for the network?
For this one we have to investigate a little bit more deep so I just used RegistryExplorer, and then loaded the SYSTEM hive. Here we have to look for the DHCP lease information related to that network from previous question. for this we have to go to this path:
SYSTEM\ControlSet001\Services\Tcpip\Parameters\Interfaces\{18c11dbd-93ab-4ca9-a804-4f4475da25b8}\Then we will find 3 folders, the same number as the Networks we found, then I noticed that Autopsy maybe was not giving the correct time for the network, instead the device timestamp, we can see the Last write timestamp and then we choose the first one.
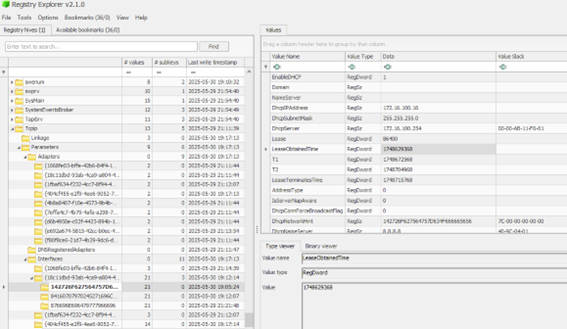
There we can see the parameter LeaseObtainedTime. right-clicking the value and then the Data Interpreter we can obtain the time format to answer the question.
Click to reveal the answer
Q4: What IP address did the device receive when connecting to the café?
We are already at the correct place from last question, we just have to look at the DhcpIPAddress and we will find the answer.
Click to reveal the answer
Q5: What was the BSSID (MAC address) of the access point they connected to at the café?
Here we have to got to load the SOFTWARE hive, and we have to locate the path
SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Signatures\UnmanagedOnce there we will find some folders, one of them is the access point. At first I looked for the name of the network we found previously, but the answer was wrong, so I found that there is a similar name of the network but adding a 2, this is the one we are looking for, I guess it makes since in the timeline this one its first, so that place must have a couple or more networks.
Click to reveal the answer
Q6: It looks like they started some sort of manifesto at the café, what is the name of the file they started to write?
In Autopsy we can load the case with the module Recent Documents once there we can find the name of the file that can fit as a title of a manifesto.
Click to reveal the answer
Q7: What is the last sentence of the manifesto?
For this one there are some places where we can check if there is more information about it, from previous question I noticed that it was inside the OneDrive folder so we can check if there is something around, but its not the case.
Searching a bit we can try with the $MFT file, there are some parsers around, but i just opened it raw and then searched for the name of the file. Just below the name of the file we can find the answer.
Click to reveal the answer
Q8: They started their research by watching a YouTube video of a speech, what is the name of the speech?
Now we should look for the logs of the browsers available, in this case there are two browsers I will start analyzing Microsoft Edge. We can see the information about the History in:
C/Users/Ernes/AppData/Local/Microsoft/Edge/User Data/Default/HistoryAnd now we can just follow the timeline of events at the table urls of the History database.
Click to reveal the answer
Q9: They continued their research by looking up a book on Wikipedia, what was the title of the book?
We are already at the correct place, just follow the search history.
Click to reveal the answer
Q10: What was the last thing they downloaded before leaving the café?
Following the history we can see that at the end they downloaded another browser, the setup .exe of this browser is the answer to the question, you can find it in the History database on the table downloads.
Click to reveal the answer
Q11: When investigating changes to network profiles on a Windows system, which event log would you examine to find entries related to these profile-specific events, using event IDs such as 10000 or 10001?
This is more like a thoerical question, so you just have to search about the name of the event logs related to network and you may find the answer.
Click to reveal the answer
Q12: Using the logs from the previous answer, when did they disconnect and leave the first café?
Now we have to look at the event log from previous question, its located at:
C:\Windows\System32\winevt\Logs\{Name of the log from previous question}I exported it and then I opened it with the event viewer of windows, choose the way you want to view the logs.
There we can find when they disconnected from the first café, we already know the name of the access point that they where conected so we have to look for a disconnection of that network. Care with the time location use the system time that you can find in details.
Click to reveal the answer
Q13: Using the same logs, when did the user arrive at the second café?
Similar to the previous question, but now search a connection to a new network.
Click to reveal the answer
Q14: What is the SSID(decoded) of the second Wi-Fi they connected to on May 30th 2025?
Here considering we obtained the last question we already know this information.
Click to reveal the answer
Q15: What IP address did the device receive when connecting to the second café?
We have to revisit Q4, here we found 3 folders, the first one was the first network tht they connected, the second folder is this new one, so we just check the DhcpIPAddress and we have our answer.
Click to reveal the answer
Q16: When did the system obtain a lease for the second network?
Following the previous question check the value LeaseObtainedTime and that’s it, just like Q3.
Click to reveal the answer
Q17: What was the BSSID (MAC address) of the access point they connected to at the second café?
Nothing new here, just the same process as Q5 searching the name of the network.
Click to reveal the answer
Q18: What was the first thing the user downloaded at the second café?
We already know that another browser was downloaded, and also we can see that there is no more logs of searchs in Microsoft Edge, so they must have changed browsers.
We now can take a look at the logs of this new browser, im using Autopsy for it, the path is similar to the one for Edge, but in this case go for this other browser. There we can go to the History and go to the downloads table, and we will find it.
Click to reveal the answer
Q19: What online forum/social media site did they visit?
Lets go to the table urls of the History database, and lets analyze the history search and we can find a famous forum/social media site.
Click to reveal the answer
Q20: What was their username on the site?
I found this information at the Login Data database inside the table logins, we are still in the browser folder from previous questions. And I also found it at the Web Data database on the table autofill.
Click to reveal the answer
Q21: What was the name of the VM they created?
For this one we can take a look at the $MFT file, this time the trick of loking at the raw data didn’t work so i did use the EZ tool MFTECmd.exe to extract the information, there we can consider to search for VM extensions and we can find the name of the VM. I just searched for .vbox and I could find the name of the VM.
Click to reveal the answer
Q22: What street was the first café on?
We have some information to work with, we just need where to find it. There is a website that can help us: wigle.net. Here we can find a wifi using a BSSID and the name of the network, and we have both. Doing a query here we can find the location of it.
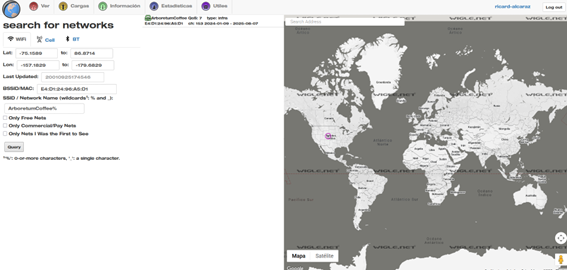
Click to reveal the answer
Q23: Investigators may want to follow up on the Wi-Fi credentials used at the first café the suspect visited. Which file stores the authentication details (including the encrypted password) for the first network?
We are almost done, the location of this file is over here:
C:\ProgramData\Microsoft\Wlansvc\Profiles\Interfaces\{Interface ID}\{Profile ID}.xmlWe can look each to find the name of the network until we can locate which is the one we need.
Click to reveal the answer
Q24: What authentication method was used to connect to the first café’s Wi-Fi?
Final question, this information is already in the same file from last question, so we are done!
Click to reveal the answer
Conlusion
I enjoyed this one, it was long but very interesting I have learned a lot from it!