XLMRat Lab – CyberDefenders

Scenario
A compromised machine has been flagged due to suspicious network traffic. Your task is to analyze the PCAP file to determine the attack method, identify any malicious payloads, and trace the timeline of events. Focus on how the attacker gained access, what tools or techniques were used, and how the malware operated post-compromise.
Documents Provided
- 236-XMLRat.pcap
Q1: The attacker successfully executed a command to download the first stage of the malware. What is the URL from which the first malware stage was installed?
Analizing the PCAP file I looked for a HTTP using a method “GET” to see what content was obtained or downloaded.
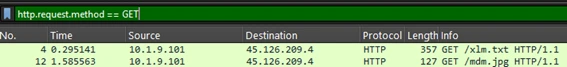
Two results pop-up from two files obtained, xlm.txt and mdm.jpg. Following the HTTP Stream of xml.txt we find this:

We can see that there are some string variables that will combine, looking at the strings we can already see a URL:
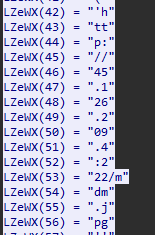
Combining the strings will reveal the answer.
Click to reveal the answer
Q2: Which hosting provider owns the associated IP address?
Here we can analyze the obtained IP address. For example using https://whois.domaintools.com/
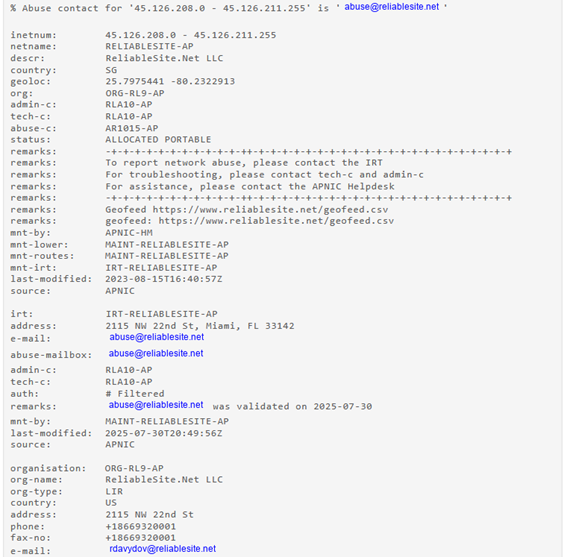
With the info we can obtain the hosting provider
Click to reveal the answer
Q3: By analyzing the malicious scripts, two payloads were identified: a loader and a secondary executable. What is the SHA256 of the malware executable?
Using wireshark we can obtain this downloaded file mdm.jpg

And we can analyze the information it contains.
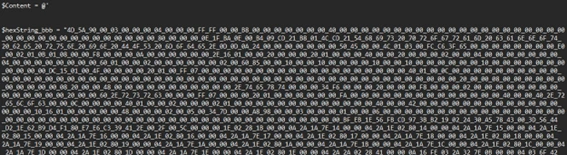
First we can see a variable of a hex string separated by an underscore for obfuscation I guess. Scrolling down we can see what is done with this variable.
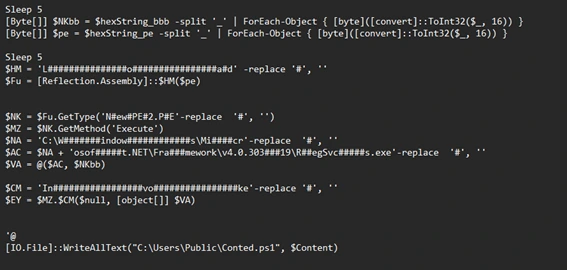
And from this code we can see that there are two hex string variables. Using CyberChef I will replace the ”_” and use the receipt “From Hex” for both of these hex strings.
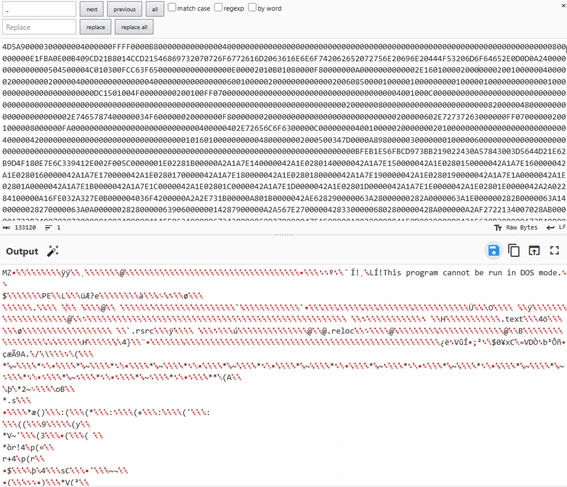
- For hexString_bbb:
- For hexString_pe:
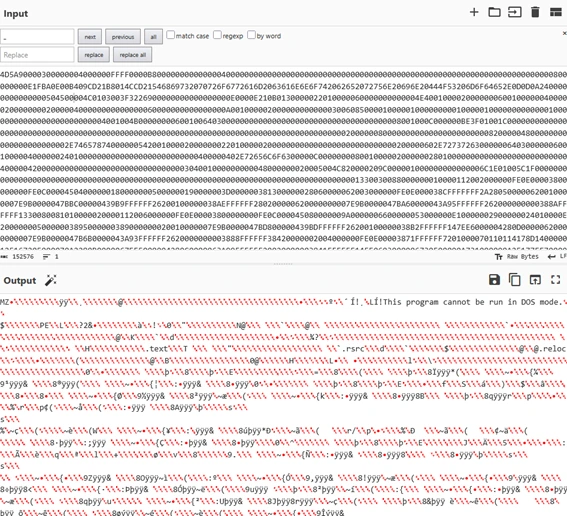
From here I save both files as an .exe, using CyberChef you can download them directly, im naming one bbb.exe and the other pe.exe referring to the variable that they come from, hexString_bbb and hexString_pe. Then im using pestudio to analyze both files and obtain relevant information. Following the code:
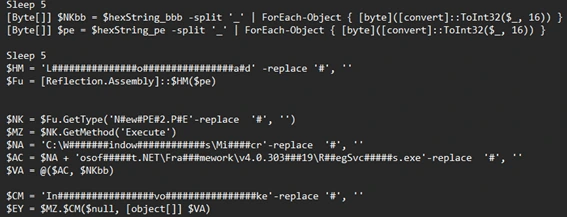
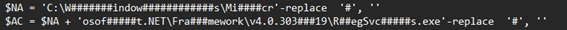
I see that the last variable $EY results in something like this, considering the name I put to the executables: Execute.Invoke($null, [object[]] @('C:\Windows\Microsoft\.NET\Framework\v4.0.30319\RegSvcs.exe', bbb.exe)
So im guessing that bbb.exe is the malware executable we are looking for. In pestudio we can see that the SHA256 hash of the file is:

Click to reveal the answer
Q4: What is the malware family label based on Alibaba?
Pestudio already provide as this information from VirusTotal.com

Click to reveal the answer
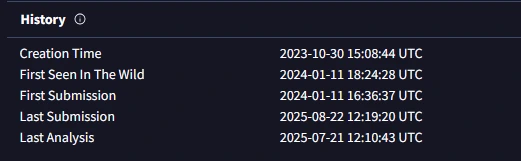
Q5: What is the timestamp of the malware’s creation?
Searching in VirusTotal we can find the date of creation.
Click to reveal the answer
Q6: Which LOLBin is leveraged for stealthy process execution in this script? Provide the full path.
In Q3 I already found the full path. Again, looking at the script inside the mdm.jpg and clearing it.
Click to reveal the answer
Q7: The script is designed to drop several files. List the names of the files dropped by the script.
We have to look again at the script inside the mdm.jpg.
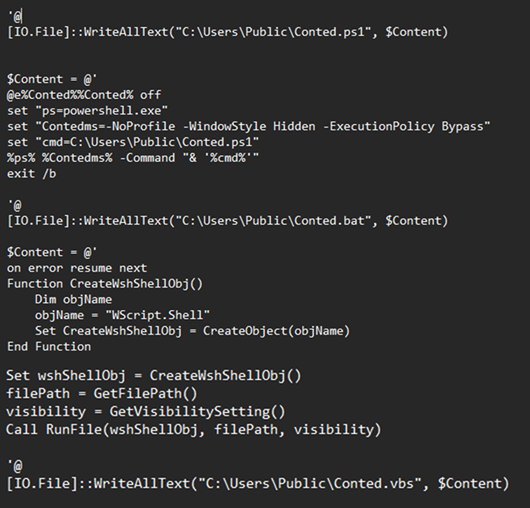
And we see 3 files where content is droped because the function used is WriteAllText, these are: Conted.ps1, Conted.bat and Conted.vbs